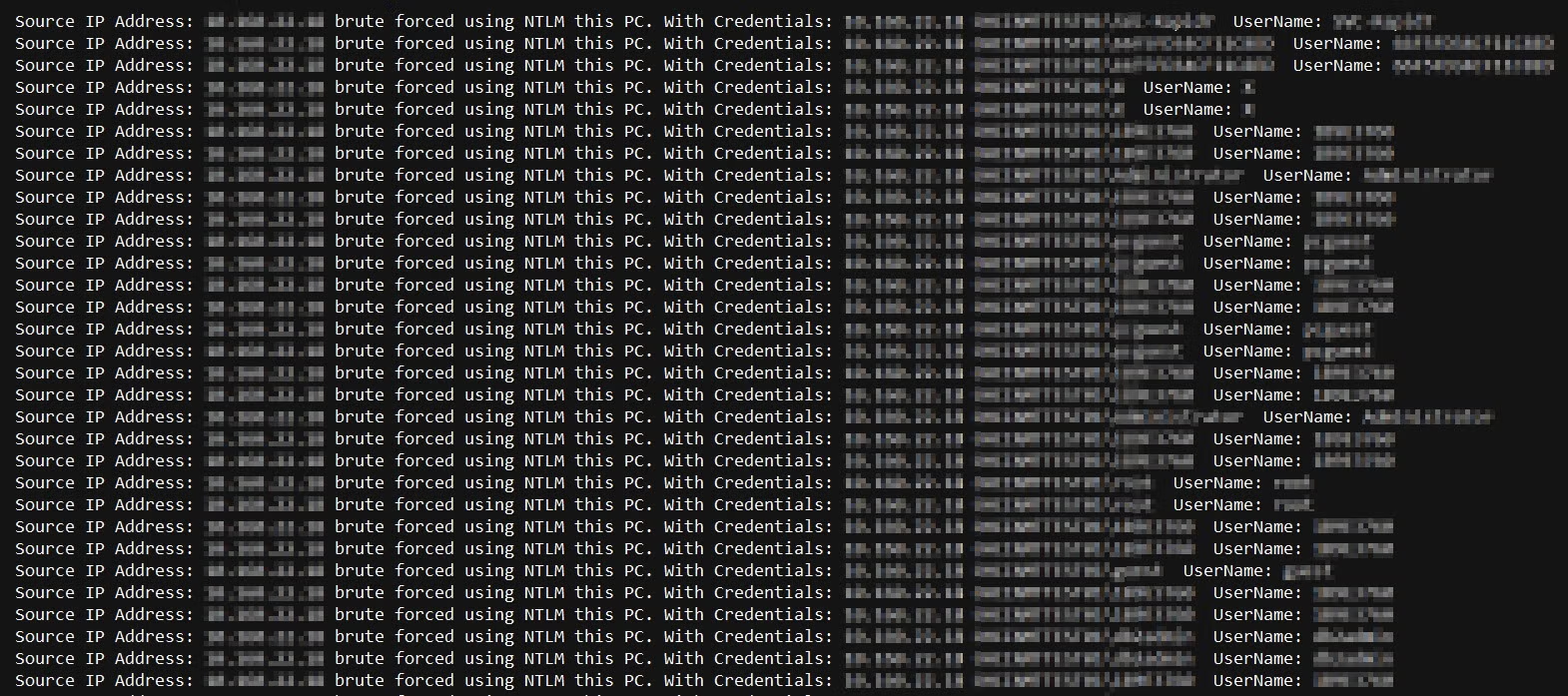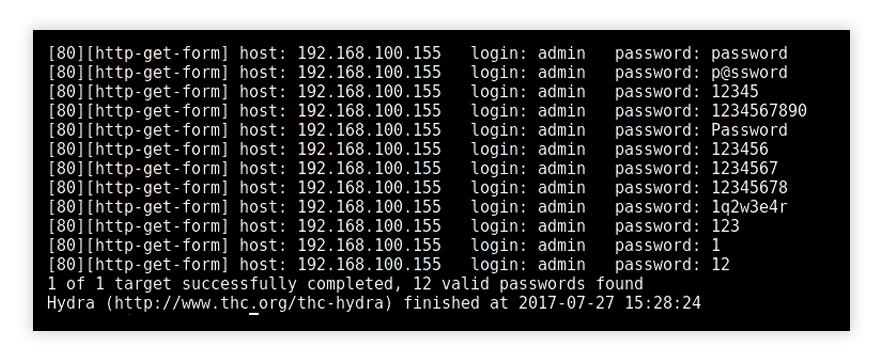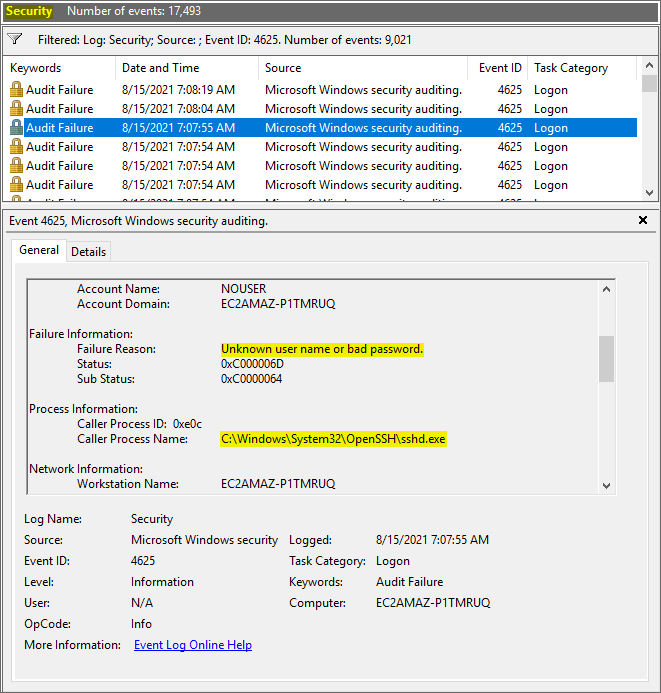
OpenSSH Brute-Force Protection - How to stop brute-force attacks on SSH protocol on Windows. OpenSSH protection on Windows.
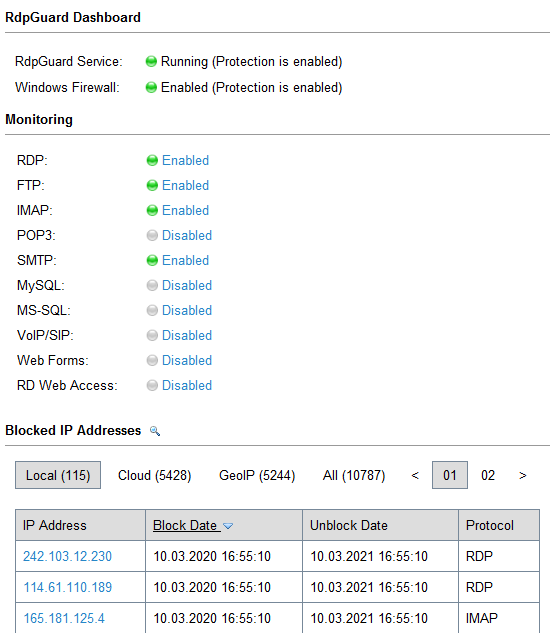
RdpGuard - RDP Protection, Stop Brute-Force Attacks on RDP, POP3, FTP, SMTP, IMAP, MSSQL, MySQL, VoIP/SIP. Fail2Ban for Windows. Stop RDP, MSSQL, FTP brute-force attacks on your Windows Server. Terminal Services Protection.




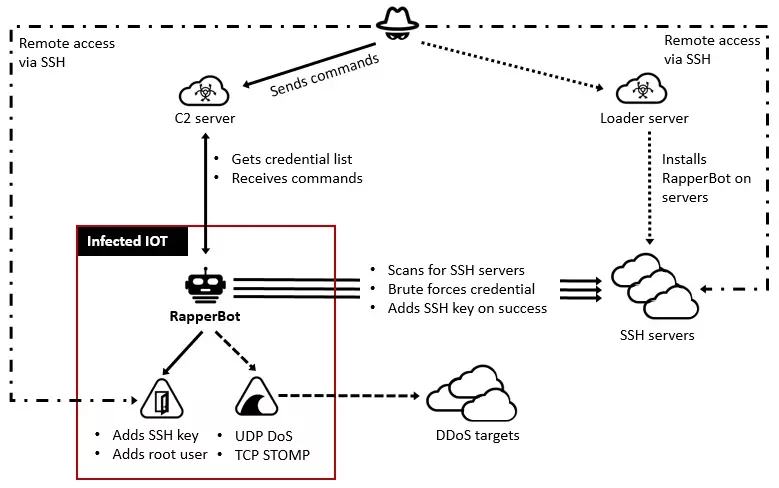


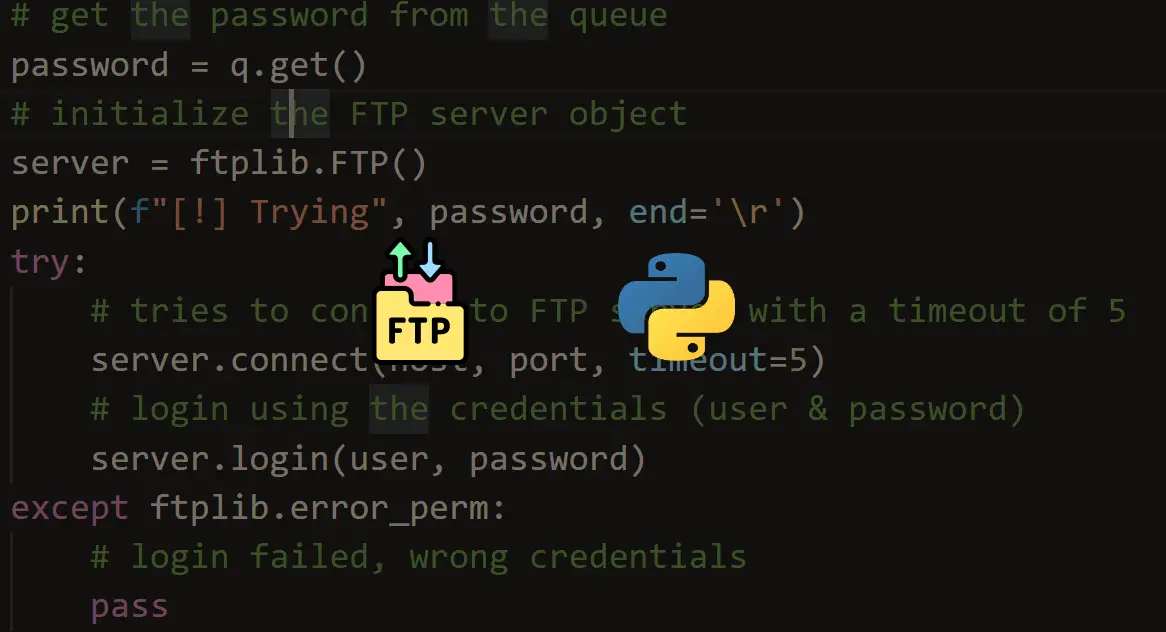





![Brute-Forcing FTP Credentials for Server Access [Tutorial] - YouTube Brute-Forcing FTP Credentials for Server Access [Tutorial] - YouTube](https://i.ytimg.com/vi/hE_Kjav323U/maxresdefault.jpg)